
Beware of These 12 Crypto Scams & Ways to Avoid Them
Crypto scams are deceptive schemes exploiting digital currencies, tricking individuals into fraudulent investments. Check out this blog on how to avoid crypto...

Crypto scams are deceptive schemes exploiting digital currencies, tricking individuals into fraudulent investments. Check out this blog on how to avoid crypto...
Crypto scams are awful to say the least. As the technology behind crypto becomes more and more sophisticated, so do the scams. One way for a crypto-entrant to stay away from scams and scammers is to do their fair share of research at their end. You can thank me later!
Due to the nature of this space, crypto demands people to possess a bit of technical knowledge. But that was the case when the internet showed up. That was probably the case when banking became popular. So with any innovation especially in technology, the learning curve is unavoidable. In fact it should be taken in the right spirit to benefit from its vastly positive disruptions while taking necessary precautions to protect your funds from being stolen, rug-pulled, or exit-scammed. This article throws light on various forms of crypto scams that we see in the world today along with ways to avoid them
This has been a common scam over the years. Scammers create accounts impersonating official project members. They send you a direct message asking if you would like their assistance in ‘recovering your wallet’ or ‘authenticating your wallet.’ The scammer then sends you a link to a phishing site that either asks for your private keys or downloads malware in your system.
How do you stay safe from this type of scam? Always check the username of the account. Each username is unique and no two usernames can be the same (applies to Twitter, Discord, Telegram, etc.).
If the scammer contacts you on Telegram, they may try this trick with new users. The scammer will update the project representative’s username in his bio section. At first look, it will be almost impossible to differentiate between the two accounts. For example, let’s take a look at a real and fake Telegram account of one of my friends, Sanjai (his PII is censored for security purposes).
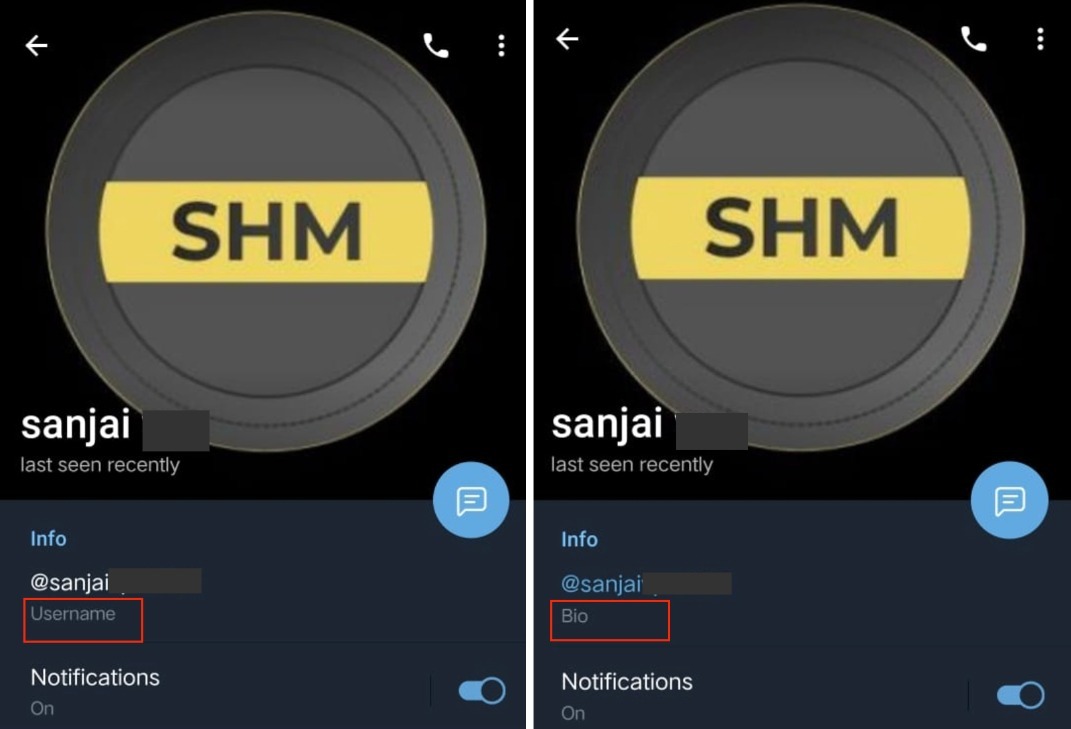
Notice the difference? The fake account on the right hand side has Sanjai’s username in its Bio section instead of next to the username. Similarly, on Discord, no two usernames can be the same. Let’s say my username on Discord is Cryptormw#3109. Check the last four digits after the #. If someone with the username Cryptormw#0001 contacts you, you can be pretty sure that it’s not me.
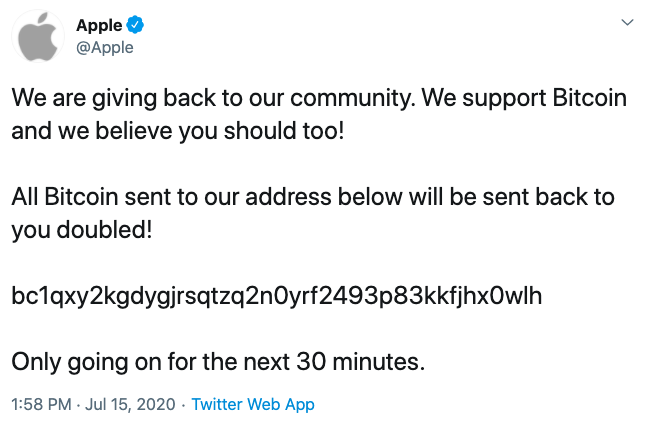
Another scam that you may come across on Twitter is the fake crypto giveaway. Graham Ivan Clark, then a 17-year-old U.S. teenager in mid 2020, hacked the Twitter accounts of high profile verified users and even the profiles of global brands like Apple and Uber. From these accounts, the hacker posted a wallet address claiming to giveaway twice the amount of bitcoin sent to the address. A total of $118,000 was siphoned off from investors in this scam.
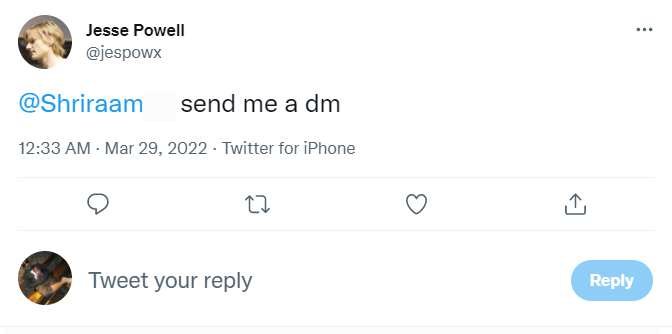
Further, if you’re tagged in a tweet or you receive a DM from a celebrity, always check their usernames. In the image below, you can see that Jesse Powell, the founder of Kraken exchange has tagged me in a tweet. Upon double-checking, I found that the real Jesse Powell’s username is @Jespow and the fake is @Jespowx. This is how scammers make subtle changes to usernames so they can trick users into giving up their seed phrases and private keys.
On Jan 24, 2022, the Coin Bureau YouTube channel was hacked in a series of hacks that targeted several other prominent crypto YouTubers. This was despite the fact that some of the hacked YouTube accounts were apparently protected by 2FA. The hacked accounts were then used to relay live videos of crypto giveaways. Such videos usually play a past recording of a live session by a public figure. An address is displayed on-screen asking viewers to send their crypto funds to the said address and receive twice the amount in return.
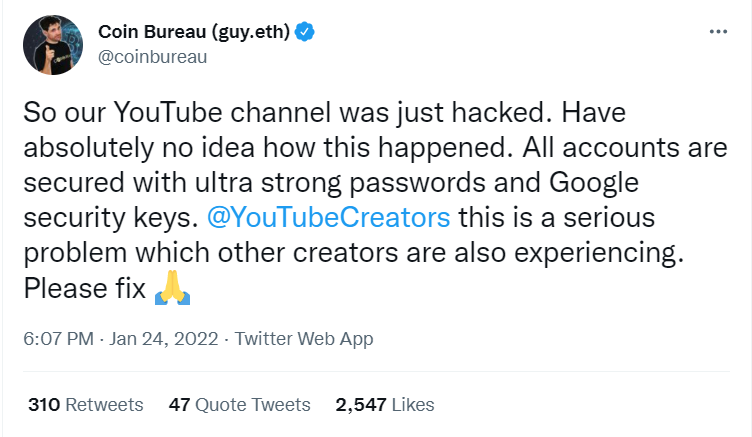
By now, one would assume that people would’ve gotten over this trick. But it still seems to nab newbies. As a thumb rule, never send your funds to anyone if they claim to offer you free money, even if they are someone who represents a genuine crypto project. Newcomers to crypto also confuse this scam with an affiliate airdrop. However, airdrops don’t work this way. They don’t require you to send funds to anyone.
Phishing refers to a type of malicious activity that a hacker employs to gain access to your personal information. It could be your email or phone number. They also get this data from darknet forums that sell users’ PII (obtained from various other hacks and security compromises). From this information, aggregate data about interests and location is filtered. Then, the hackers send out meticulously crafted emails targeting the users.
For example, if the hacker knows that you’re a user of the crypto exchange Binance, then they may send you an email stating that “Binance is giving away free NFTs to 1000 people on a first come first serve basis. Claim your NFTs fast!!” The message conveys a sense of urgency to act.
Attached to this message will be a link. The link may direct you to a website that looks exactly like binance.com. Except that it’s not binance.com but biance.com or binace.com. Once you log in to the fake website, the hacker can figure your password, since the fake website is connected to a database that collects your information and does not typically provide any other real service.
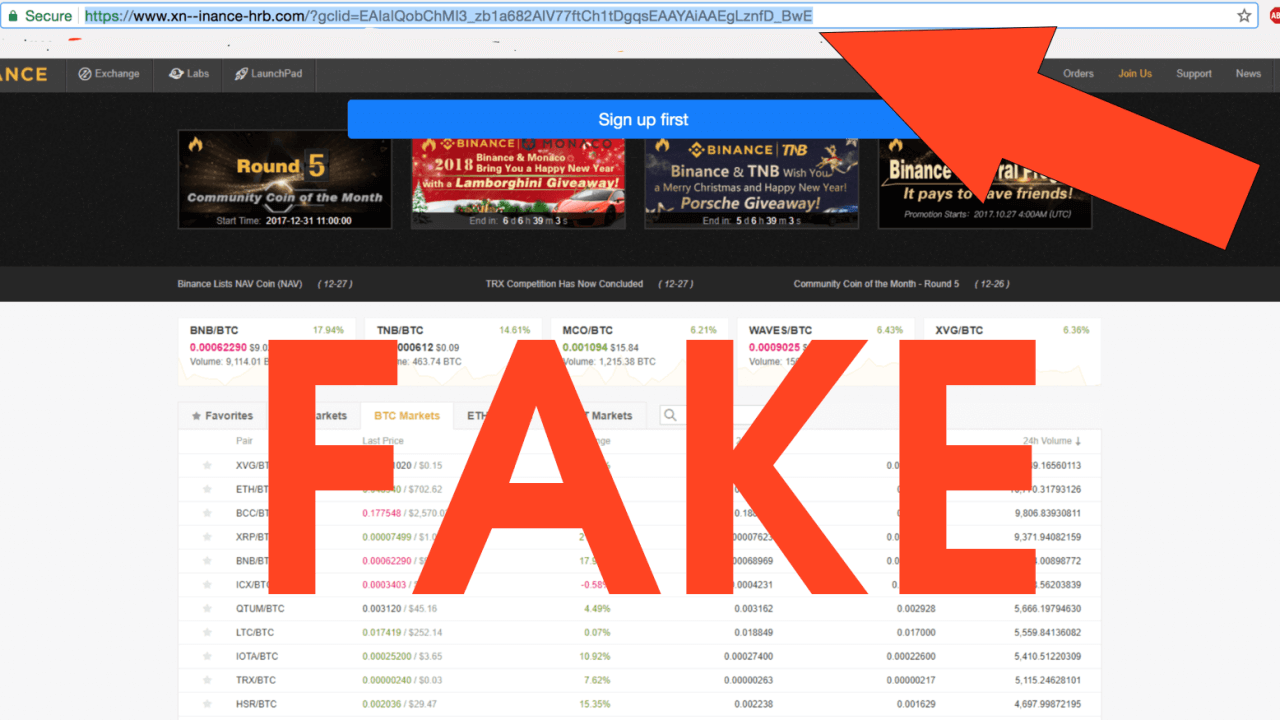
Now if you’re a seasoned crypto user, you’d know that Binance provides a feature that allows users to verify the authenticity of emails. Using an anti-phishing code, account holders can verify the sender of the email. You can avoid phishing if you use emails that haven’t been “pwned”. It’s also important to change your passwords once in a while. Check this website to know if your personal information may have been compromised in a security breach previously.
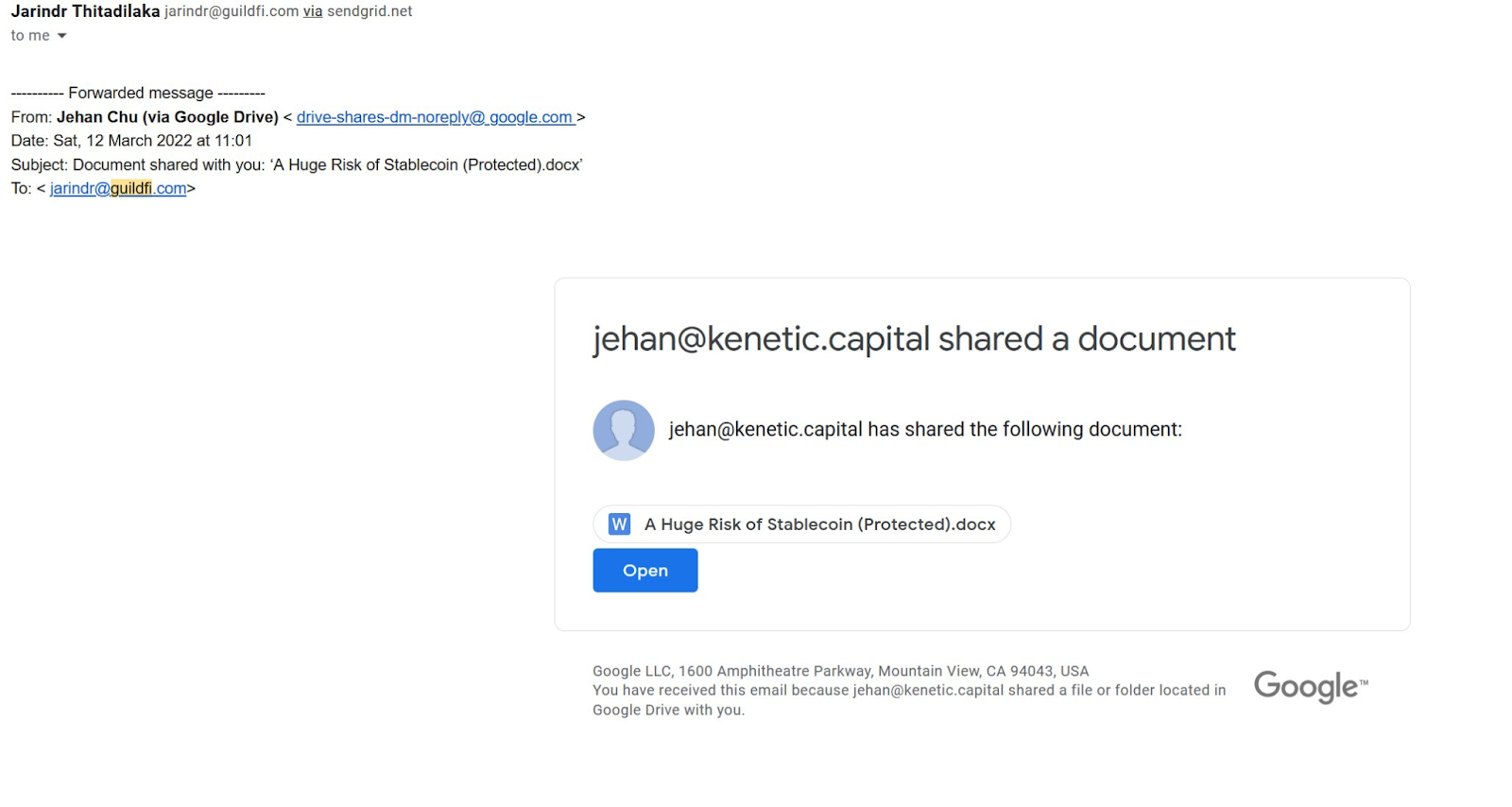
This is a much more detailed method of a phishing attack. This attack targets a certain individual or a group of individuals. The attacker takes painstaking efforts to research the individual/group they’re targeting. The most recent example of a spear-phishing attack is that of Arthur Cheong, the founder of the crypto investment firm Defiance Capital, who ended up losing NFTs worth over 1.7 million.
To pull off this attack, Arthur was sent an email from one of his portfolio companies with industry-relevant content. When he downloaded a file attached to the email (which he claims that none of the installed anti-virus software picked up as malicious), the attackers first managed to gain access to his device, then his private keys (from a recovery file or seed saved digitally), and swindled the NFTs from his wallet. Arthur later said that the attack was orchestrated by BlueNoroff, a unit of the Lazarus group, a notorious group responsible for large-scale attacks on the banking sector. Most notable is the attack on Bangladesh’s Central Bank in 2016. This group is particularly good at exploiting trust.
If it’s not from PlayStore, AppStore or any other marketplace that you trust, then don’t consider downloading the application. Even trusted platforms like the Google Chrome Web Store, struggle with removing fake plugins that pop up like bees from a hive.
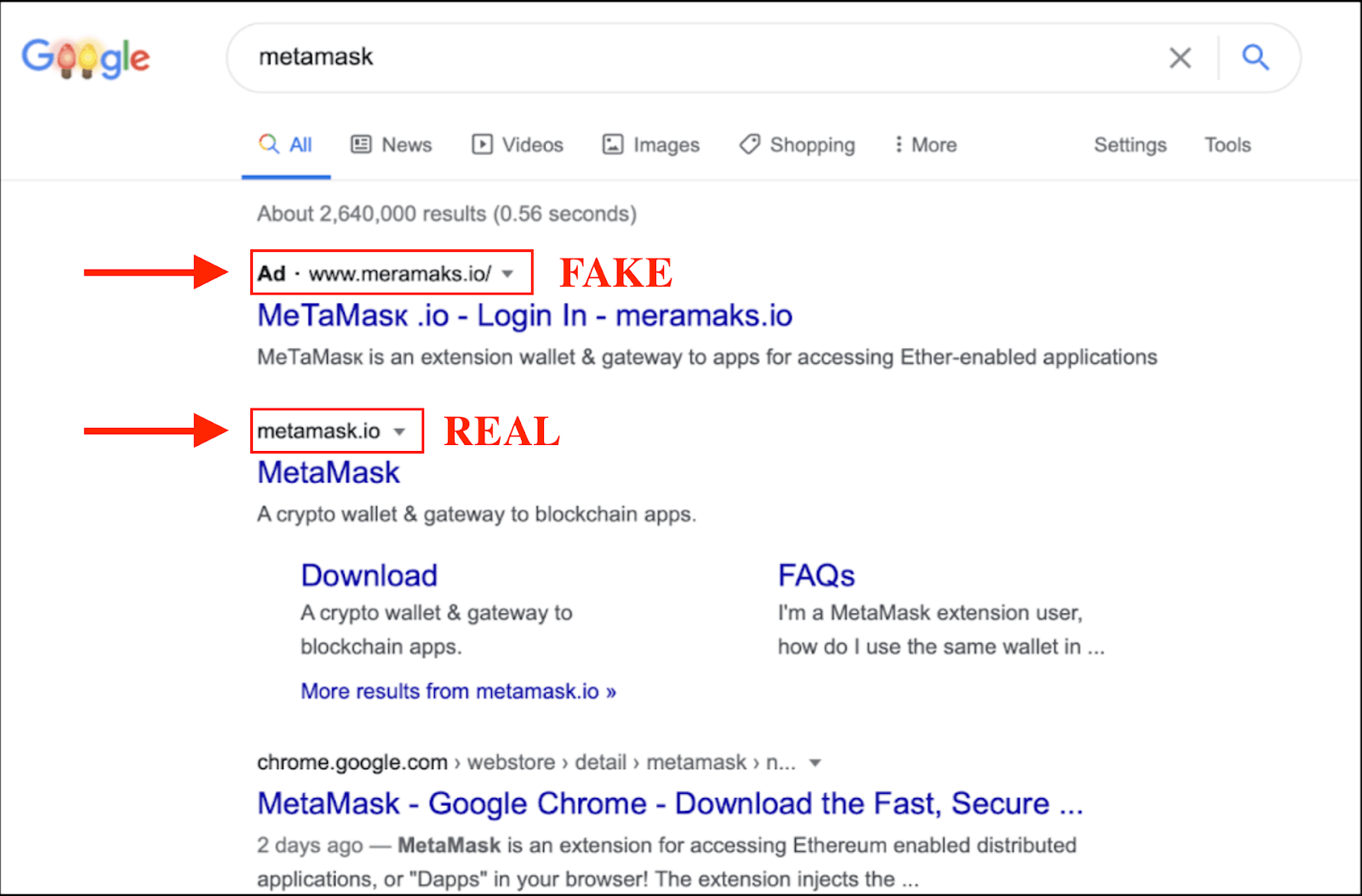
Fake Metamask Plugin: Back in Dec 2020, Ciphertrace published an alert from Metamask users who claimed their funds were stolen. The victims downloaded a fake Metamask plugin from a fake website with the URL installmetamask.com. Metamask’s official website is https://www.metamask.io/.
The users were scammed as the fake website was even running relevant keyword-specific ads on Google. In the image below, see the fake URL meramasks.io in the ad section of the search results.
When restoring/updating your Metamask, Binance Wallet, or the Solflare wallet on a browser plugin, always use the links from the official website to download the plugin. For example, if you’re installing the Metamask plugin on Google Chrome browser, it is recommended that you always visit metamask.io first.
Just so you know, Ethereum began its transition to Ethereum 2 (now called “Merge”) in December 2020. That way the network can start using the Proof of Stake (PoS) consensus mechanism which is apparently more scalable and takes only a fraction of energy compared to its existing Proof of Work (PoW) consensus mechanism. Several scammers in the meantime exploited the naming convention (or confusion so to speak of). ETH holders were randomly asked to transfer their ETH 1 to a fake smart contract and convert it to ETH 2 in the name of safeguarding the value of their coins.
So should you convert your ETH 1 to ETH 2? The simple answer is NO. The basis of this scam is the idea that ETH 1 and ETH 2 are two different coins. But they’re not! Ethereum is simply upgrading their network. That’s also one of the reasons why Ethereum started referring to the word “Merge” for the migration to PoS. You don’t have to do anything to convert your coins to the ETH 2 standard. After the Merge, your Proof of Work ETH should simply exist on the Proof of Stake Ethereum chain. Simple as that.
CO scams were rampant during the 2017 ICO boom. A 2018 study reported that 80% of the ICOs from 2017 were scams. Now they’re few and far in-between. Scammers are instead focusing on building their own smart contracts (web3) instead of developing centralized websites (web2). An ICO scam is basically the project team luring investors to crowdfund their ‘revolutionary’ crypto startup idea which doesn’t take off. Once the ICO ends, the team vanishes without any trace of the funds. Investing in ICOs, IDOs, IEOs, STOs, and more recently, IGOs have been the allure to investors with a higher risk appetite. However, conducting due diligence before going all-in into an investment is crucial.
Check if the project team is transparent and read their whitepaper & roadmap. Is the project launching on a never-before-heard-of launchpad? Then it’s better to take the wait and watch approach. It’s generally safer to participate in IDOs and IEOs on launchpads and exchanges that have always introduced genuine projects to their user base.
Ponzi schemes do not create any real value. They are pyramids that pay past investors with capital raised from current investors. They create the illusion of growth and profit when there’s no real product or service. Forsage.io is an example of a pyramid that grew rapidly like mushrooms after a rain.
When a couple of friends called and urged that I invest in Forsage’s contract, it raised all the red flags for me. First off, there was a minimum investment. Secondly, I’d have to ‘lock’ my funds for a specific time period. And the worst of them all, I’d have to ‘refer’ three other people to get involved (that’s how I got the call in the first place). This was a classic Ponzi. I advised my friends to stay away from the platform. Shortly after, the Philippines Securities and Exchange commission flagged Forsage as a pyramid scheme. Six months later, the U.S. state of Montana issued a cease and desist order publicly denouncing Forsage. The magnanimity of this scam was that it managed to reach a number of local communities in a very short span of time.
But how do you identify a Ponzi scheme? Some Ponzis are so good at concealing themselves that most people don’t know they’re in a pyramid scheme until they lose their money. One way to identify a Ponzi is to check the project’s revenue model. Ask yourself some of these questions. Are there any noticeable products or services offered? How is the business funded? Does the ROI sound too good to be true? Are you asked to refer them to more people or promote the platform for incentives? Does your investment have a lock-in period that keeps extending? Are you being denied access to your funds? Then it may well be a Ponzi.
A rug pull is a crypto scam that makes you think that everything’s alright until it’s not. Rug pulls are notoriously deceptive in nature. A project team will start with developing a legitimate crypto / high yield DeFi project to garner investors’ attention. They will appear to stick to their roadmap and develop the project, partnering with other legitimate crypto projects. They further get themselves listed on lesser known DEXs and CEXs typically.
Just as everything seems to be going well, the project goes offline along with your funds. As you try to wrap your head around how and why this happened, somewhere in the corner of your mind, there’s a voice screaming “how did I miss the signs?”
The most notorious crypto DeFi rug pull of 2021 is the Squid Game Token, the one which rode on the hype of the Netflix show of the same name. The Squid Game Token (SQUID) developers (not related to the Netflix show at all) launched their DeFi project on the Binance Smart Chain and listed SQUID on DEXs like PancakeSwap and DODO. They then created a liquidity pool where investors would lock in BNB in exchange for SQUID tokens.
Unsurprisingly, the Squid Game Project used a GameFi economic model in which users can use their SQUID tokens to play games that rewarded them with ‘marble’ tokens. Apparently, to sell SQUID, you need marbles.
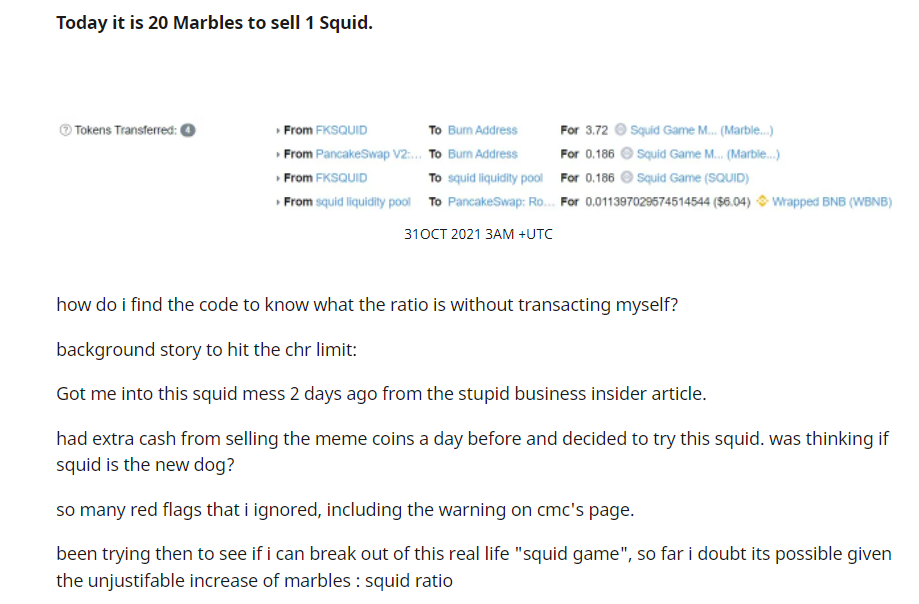
As the project gained in popularity, more and more people began locking their BNB into the liquidity pools on PancakeSwap and DODO in exchange for SQUID. As a result, the price of the token quickly rose from a few cents to $2861 USD. To be precise, if you’d invested a dollar in SQUID, the ROI you would have seen is 286100% in the span of a few days.
But here’s the catch. When investors tried to swap SQUID for BNB to take profits, they were unable to do so. The project developers had written malicious code that prevented others from selling the token on decentralized exchanges (DEXs). They also held a large number of SQUID tokens themselves, so they easily swapped them for all the BNB in the liquidity pool. A total of around $2.5 million dollars in BNB was lost in this scam.
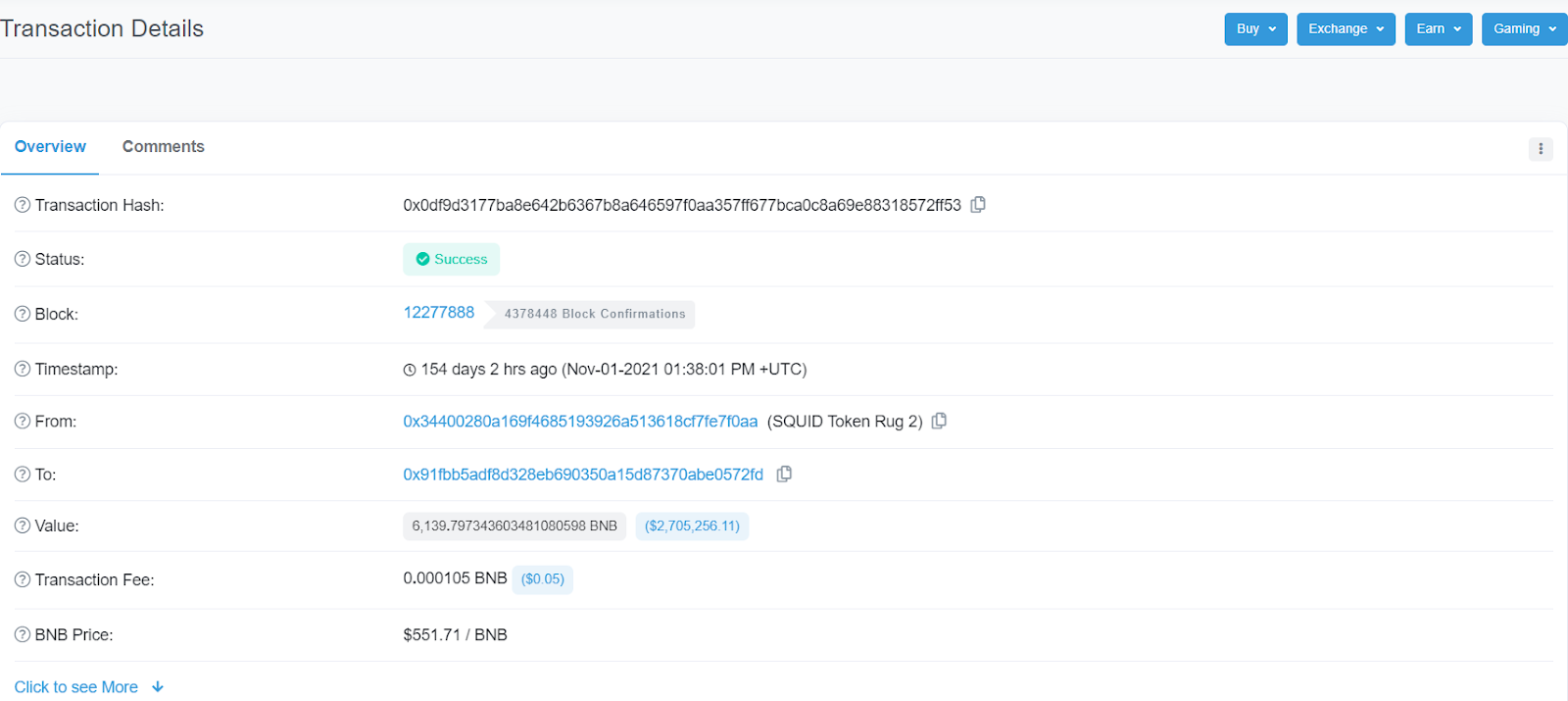
Are you a founder of a crypto startup? Then, getting your crypto listed on top international and regional crypto exchanges is a huge step. It means that your project is getting the exposure that it needs. Exchanges like Binance, Gate, KuCoin, FTX, Coinbase, Liquid, Huobi and Kraken are a few among the top exchanges. Most of these exchanges have a very strict screening process. For example, Binance has only listed around 600 cryptos from among 18,719 tokens (as of March 2022). There’s a wide gap between the number of projects that pop up every day and those that are listed on top crypto exchanges. More or less similar to your stock market, albeit, without government regulations (at least as of March 2022).
Exchanges like Gate do not charge a fee for listing crypto and can only be contacted through official representatives. However, fraudsters take advantage of this. They impersonate representatives by creating fake LinkedIn profiles and domain email IDs of a real crypto startup. They charge a hefty fee or a security deposit for listing your crypto and then disappear with your funds.
Not falling for this scam is easy. Check the URL of the exchange website you visit. Always contact representatives through the channels listed on the official website. Certain exchanges like Kucoin provides an ‘official media verification’ feature that allows you to verify the telephone number/email/Twitter and other social media handles of official representatives.

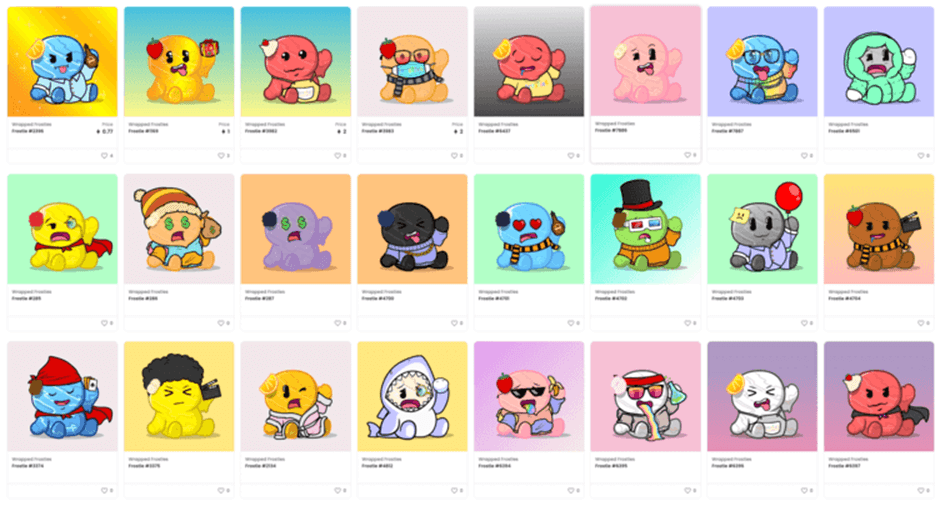
In March 2022, a couple of 20-year-olds made headlines for all the wrong reasons. Ethan Nguyen and Andre Llacuna launched their NFT based project, the Frosties recently. The Frosties were NFTs based on frozen ice-cream desserts and were advertised to provide lucrative benefits to their holders. The investors who bought the Frosties were promised the following:
But none of this happened. As soon as the sale concluded, the Frosties website went offline and its Discord and Twitter were taken down, but not before tweeting “I’m sorry.” It was ironic that the fraudsters would apologize. At least they were letting people know that the rug was pulled from under their feet which was around $1 million dollars. The icecream characters transformed back to normal JPEGs.
Victims of the scam reported the incident to the U.S. Federal agencies. The IRS and the Department of Homeland Security arrested the duo on March 24, 2022. The duo had almost sold off another NFT project named the ‘Embers’ valued at 1.5 Million USD. They now face charges of conspiracy to commit wire fraud and money laundering.
NFTs are the craze today, with every industry finding a use case in them. But not all of them will make it to the light of day. @Mr0chill from Quantum Tech, a project building interactive NFT experiences, recommends that you don’t respond to DMs that offer you to buy the next big 100x NFT. If it sounds suspicious, then it most likely is.
Two-step verification adds a second layer of security to your crypto wallet or account. When you use this service, you will be asked to re-verify your identity using a code sent by text to your phone or by email. Or you could simply install apps like Google Authenticator which will generate a new code every few seconds which you could use as 2FA.
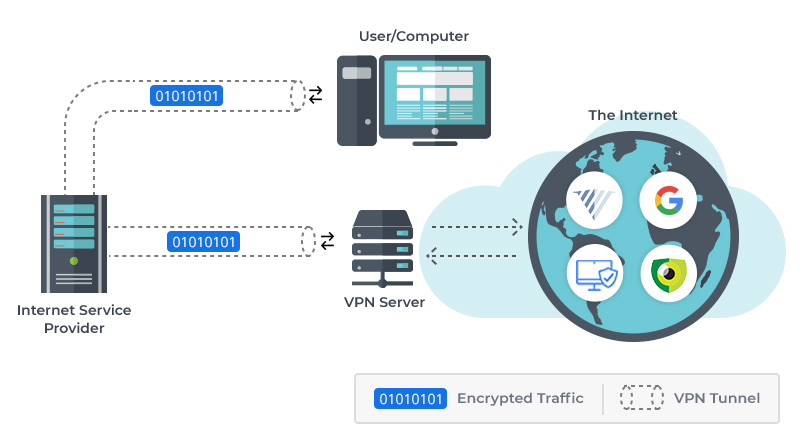
Avoid using unsecured public Wi-Fi on your devices. When you’re not at home, use a VPN, or virtual private network, to browse the web. This encrypts your traffic as well as reroutes your data packets through VPN servers, making it considerably more difficult to intercept.
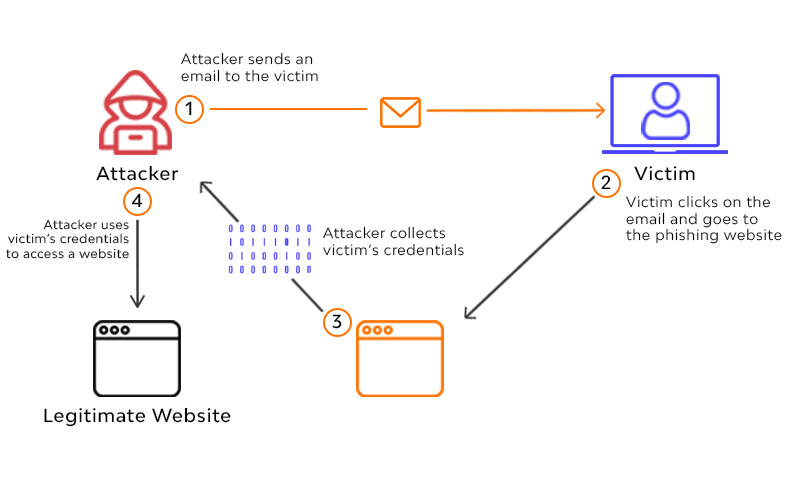
One of the most common frauds you see in the crypto industry is phishing. As discussed previously, phishing is a sort of online fraud in which traps are set up in order to get sensitive information such as credit card numbers or passwords. These traps come in the form of phishing emails, malicious websites, or enticing advertisements.
To avoid phishing attacks:
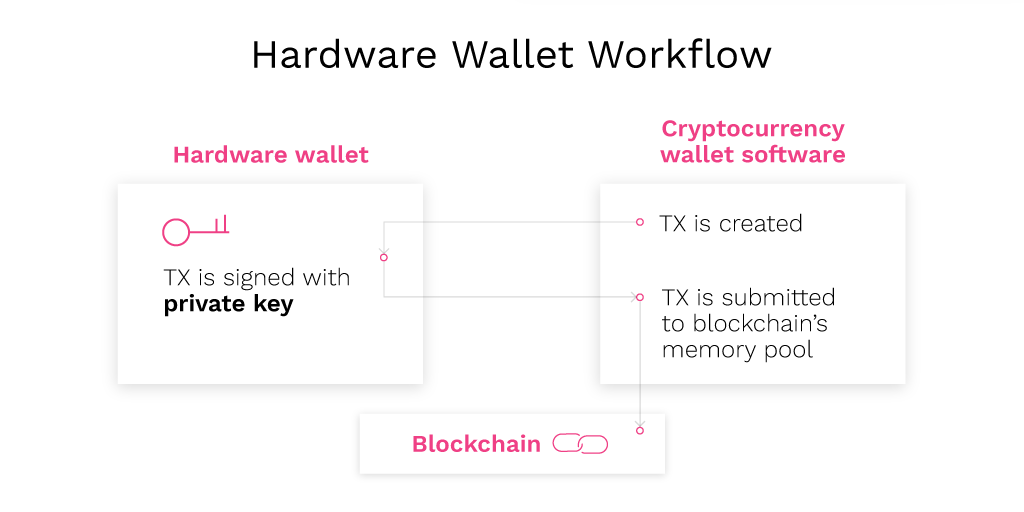
A cold wallet is a physical device that keeps your cryptocurrency completely offline. Many crypto investors have a habit of keeping the cryptos under their custody and use a hardware wallet. Make sure to plug your hardware wallet into a power outlet when generating the seed phrase to keep it as cold as possible.
Popular Cold wallets:
Check the SSL (Secure Sockets Layer) certification of a website to see if it is secure. This is one of the easiest ways to improve your internet security. When shopping online, check if the URL begins with “HTTP://” or “HTTPS://.” The latter means your connection is encrypted and secure. It’s important to check that the website is secure to prevent any loss of sensitive data.
Scams act as a deterrent to a quicker crypto adoption. In order to bank the unbanked people, crypto should be easier and safer to use. Though the total amount of funds lost in crypto scams pale (less than 0.5% was owed to illicit transactions in crypto in the year 2020) in comparison to the scams we are used to seeing in traditional finance, we must do everything in our power to prevent them.
Yes more governments will start recognizing and regulating cryptocurrency in the future which can help to protect small time investors. And as technology around this space evolves, crypto will become more secure and user-friendly. But as you would have realized by now, the scams would also evolve. It is our responsibility to make this space safer for yourself and newcomers.
And, if you were fortunate enough to get into the blockchain, crypto, and Web3 space early on, we encourage you to help educate your friends and family on how to traverse this ecosystem. Because, as with every new technology, it’s easier to protect yourself from crypto scams if you get used to the workings of this space.
Layer 1 Crypto Projects 2022 | Types of DDos Attack | What is AMM in Crypto | How to Mint Crypto | What is a Dao Crypto | How to Avoid Crypto Scams | Types of Cryptocurrency Scams | What is Decentralization | What is Miner Extractable Value | What is White Paper in Cryptocurrency | How to Make and Sell NFT | Learn Web 3.0 | What is a Blockchain Node | Deploy ERC20 Token | Best Blockchain Bridge | Peer to Peer Money Transfer | Pros and Cons of Blockchain Technology | Gas Fees Blockchain | What is Layer 1 Blockchain | Blockchain Technology Explained
Opinions expressed in this publication are those of the author(s). They do not necessarily purport to reflect the opinions or views of Shardeum foundation.
About the Author(s) :
Shriraam Sekar is a crypto writer/marketer involved in the space since 2019. He covers Layer 1s, DeFi, NFTs, Metaverse, GameFi, SocialFi, and crypto regulations. Follow him on Twitter for collaboration related to crypto/Web 3.0
Shuwam Rana is a Technical Analyst, Digital marketer and SEO expert with a passion to help businesses grow. He also has an engineering background. You can follow him on Twitter