Blockchain Security – A Complete Guide
Blockchain security is a risk management technique that aims to secure transactions, ensuring trust and immutability. Explore its types, and importance in safeguarding transactions and...

Blockchain security is a risk management technique that aims to secure transactions, ensuring trust and immutability. Explore its types, and importance in safeguarding transactions and...
A blockchain is, of course, a shared ledger or distributed database spread out among various nodes in a computer network. Acting as a database, it stores digital information in electronic format. Although most famous for their role in cryptocurrency systems like Bitcoin, blockchains are also utilized for maintaining secure, decentralized records of transactions in various other fields.
What makes blockchain cybersecurity technology unique is that it provides a guarantee of fidelity and security when it comes to recording and storing data. The beauty of this system is that it generates trust without needing a trusted third party. With blockchain, you can rest assured that your information is protected and secure, no matter the field of application.
Cryptography is used to secure transactions and ensure that only a particular asset’s owner can access and use it. However, some common security concerns with blockchain technology include the potential for 51% attacks, and vulnerabilities in smart contracts.
The way data is structured is one of the key differences between a traditional database and a blockchain. In a blockchain, information is grouped together in sets called blocks, each with a specific storage capacity. Once a block is full, it is closed and linked to the previous block in the chain, forming a continuous stream of data known as the blockchain. Any new information added to the chain is compiled into a new block that is also added to the chain once it is full.
This differs from a traditional database, which structures data into tables. As the name implies, a blockchain structures data into blocks that are strung together. This unique structure creates an unalterable timeline of data when implemented in a decentralized manner. Once a block is filled, it becomes set in stone and is permanently part of the blockchain database. Furthermore, each block in the chain is assigned an exact timestamp when it is added to the chain.
Blockchain cybersecurity depends majorly on the blockchain types. For example, public blockchains are more secure than private blockchains because they are decentralized and have many users. Private blockchains are less secure because they are centralized and have fewer users. Public blockchains offer more efficient and transparent transactions, and private blockchains can better protect users’ identities and assets. Bitcoin, for example, uses a Proof of Work consensus algorithm, while Ethereum uses a Proof of Stake algorithm. These algorithms determine how much trust the network participants put into the blockchain.
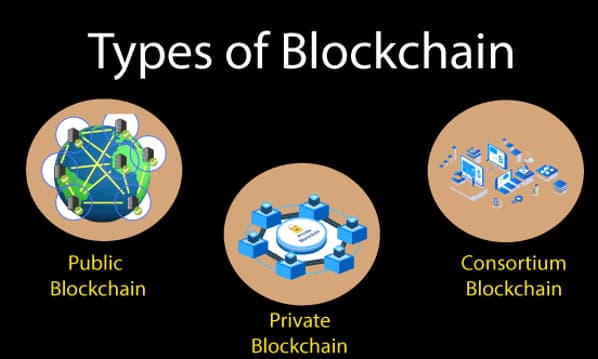
Let’s understand blockchain and security in different blockchain types:
Have you ever wondered how secure and transparent public blockchains like Bitcoin really are?
Well, here’s the scoop: public blockchains allow anyone to view transaction history and create new transactions. While this openness can make public blockchains slow and expensive, it also means they are more secure than their private or permissioned counterparts.
In fact, it’s much harder for bad actors to pull off a 51% attack on a public blockchain than on a private one. So the next time you hear about the power of public blockchains, you can rest assured that they are a secure and decentralized option for managing transactions.
A blockchain network that functions within a confined setting, like a closed network or under the management of a single entity, is classified as a private blockchain. Despite operating similarly to a public blockchain by utilizing peer-to-peer connections and decentralization, this type of blockchain operates on a much smaller scale. Private blockchains are typically run on a limited network within a company or organization, and participation and computing power are typically restricted to authorized individuals.
When it comes to a private blockchain cybersecurity network, the overseeing organization is responsible for establishing permission levels, security measures, authorizations, and accessibility. This means that the organization can decide which nodes can view, add, or modify data to maintain blockchain security. Additionally, they can restrict third-party access to specific information, providing additional security and control over the network.
The Permissionless blockchain has no limitations or controls over participation, making it completely decentralized. Every user can join the consensus and validate data without requiring approval from an administrator.
The most remarkable feature of a permissionless blockchain is the transparency of transactions, as it has an open network allowing everyone to participate. Additionally, it is an open-source development that allows users to make necessary changes as required. Although it has an anonymity clause, it is not absolute, and there are exceptions to it when making changes.
Permissionless blockchain is the absence of central authority as it is open to every user. It is widely used for tokens and digital assets that serve as incentives for participation. This results in efficient and effective operations, leading to its growing popularity.
A permissioned blockchain is only accessible to a limited number of authorized users. This means that the distributed ledger can only be accessed by those who have been granted permission by the administrator. These users are given specific privileges enabling them to perform certain actions. Unauthorized access to the ledger is not permitted, ensuring enhanced security and privacy.
Permissioned blockchain provides an additional layer of security, making it a popular choice for large companies and organizations where data security is paramount. Permissioned blockchain is ideal for business operations, supply chain management, contract creation, and payment verification.
One of the key features of permissioned blockchain is transparency, which is based on the objectives of the organization. The administrator can easily track every action taken by the user, ensuring accountability and making it clear who is authorized to make changes.
While a permissioned blockchain lacks a central authority, it allows a private group to authorize decisions. This feature, combined with enhanced security and privacy, makes permissioned blockchains a valuable asset for private entities and companies.
Blockchain cybersecurity is a new and innovative field that uses blockchain technology to protect information. Through blockchain and cyber security, businesses can ensure that their data is secure and control who accesses it. Additionally, blockchain cybersecurity can help to protect society by helping to prevent cyberattacks.
The level of security required for a blockchain project will vary depending on the sensitivity of the data being stored on the blockchain and the potential threats faced by the project. However, some basic security measures that could be implemented for a blockchain project include encrypting data stored on the blockchain, using multiple signatures for transactions, and using a trusted third party to manage private keys.

Fraudsters can attack blockchain technology in several ways and render blockchain cybersecurity measures taken not enough. For example:
A phishing attack is a malicious blockchain cybersecurity attack that involves impersonating a trusted source in order to deceive victims into disclosing confidential information, such as sensitive financial data or login credentials. Cybercriminals often use this method to steal cryptocurrency from unsuspecting victims by sending them fake links that redirect them to fraudulent websites resembling legitimate cryptocurrency exchanges or wallets.
These fraudulent websites typically prompt users to enter their login credentials, which the attacker then captures to gain unauthorized access to the victim’s cryptocurrency account and steal their digital assets. Due to the high risk of such attacks, the demand for skilled engineers and developers from blockchain security companies to implement robust security measures for blockchain networks has increased significantly, leading to high salaries in various countries.
A routing attack is a potential threat to blockchain security, which occurs when attackers intercept data during its transfer to internet service providers. This attack can lead to network disruption, causing incomplete transactions. Detecting and preventing routing attacks can be a challenging task, but there are measures that can be taken to mitigate the risk. One such measure is encrypting data before transferring it, making it difficult for attackers to access and interpret the information.
Additionally, node operators can monitor their networks for suspicious activity and be on the lookout for signs of a potential routing attack. Hiring expert crypto auditors to evaluate the security measures and identify any vulnerabilities that could be exploited is also advisable. With proper security measures in place, the risk of a routing attack can be significantly reduced.
Sybil attacks are a type of attack in which a malicious user creates multiple fake identities to gain network control. Sybil attack can be made by creating multiple accounts on a blockchain or multiple network nodes. Sybil attacks can be used to cause a 51% attack on a blockchain or double-spend coins.
In a blockchain network, a 51% attack occurs when a malevolent user gains control over more than 50% of the blockchain’s mining power. This enables the attacker to mine blocks at a faster rate than other participants, granting them the ability to disrupt the confirmation and sequencing of new transactions. By doing so, the attacker can modify portions of the blockchain and reverse transactions.
The security protocols of the blockchain can be circumvented by a 51% attack, causing varying degrees of damage depending on the attacker’s mining power. The severity of the attack is also linked to the hash power held by the attacker; the higher the percentage, the greater the likelihood of success and the damage inflicted.
Code exploitation is a type of attack that targets vulnerabilities in the code of a blockchain system. This can happen when a hacker identifies a weakness or flaw in the programming language used to build the blockchain network, or in the smart contracts that run on the network.
Exploiting these vulnerabilities can allow the attacker to gain access to the system and manipulate it to their advantage. For example, an attacker could exploit a vulnerability in a smart contract to siphon off funds from the network or manipulate the results of transactions.
To prevent code exploitation, developers need to ensure that the code they write is secure and that they regularly monitor the network for vulnerabilities. They can also use code analysis tools and penetration testing to identify weaknesses in the code before attackers can exploit them.
In blockchain security, private keys are the unique identifiers assigned to each user that allow them to access and transact on the blockchain network. These private keys are essentially cryptographic keys that prove ownership of a particular blockchain asset, such as a cryptocurrency or a digital asset. If a private key falls into the wrong hands, it can be exploited by cybercriminals to alter information in the blockchain under the permissioned user’s identity.
For instance, in 2016, $73 million worth of Bitcoin was stolen from the cryptocurrency exchange Bitfinex due to stolen keys. This led to authorities identifying stolen keys as the primary source of the theft. To prevent this type of attack, it is crucial to store private keys securely and use multi-factor authentication to protect access to them.
Computer hacking is a major threat to the security of blockchain networks. Even with the use of advanced cryptographic protocols, hackers can still find vulnerabilities to exploit. One common type of computer hacking in blockchain security is known as “social engineering.” This is when attackers trick users into revealing sensitive information, such as their private keys or login credentials, by posing as a trusted entity.
Computer hacking in blockchain security might be done through “malware.” Malware is malicious software that can be used to infect a user’s computer and steal their private keys or other sensitive information. Once the attacker has gained access to the private keys, they can easily steal the associated cryptocurrency.In 2019, $13 million worth of cryptocurrencies was stolen from the Bithumb cryptocurrency exchange in South Korea, with an internal actor being the prime suspect.
Numerous security testing tools are available to help identify potential vulnerabilities. However, due to the unique nature of the blockchain, even the most comprehensive testing may not always reveal issues. Developers and businesses should familiarize themselves with the possible attacks and adopt mitigation strategies. There is no one-size-fits-all answer to this question, as the best blockchain security testing tools will vary depending on the organization’s specific needs. However, some common tools used for blockchain security testing include static code analysis tools, dynamic code analysis tools, and penetration testing tools.
Blockchain penetration testing is used to root out the possible weaknesses in a blockchain system. There are a few core measures taken in effective blockchain penetration testing, namely functional testing, performance testing, API testing, security testing, integrating testing, and more.
These are usually the steps to complete blockchain penetration testing for a project:
In this phase, information is collected for understanding and analyzing functional and business requirements. The blockchain security testing team collects information about the blockchain network such as its architecture, design, and implementation details. This information helps the testing team to understand the blockchain network’s functionality and business requirements.
The testing team also prepares a threat model which includes analyzing the blockchain architecture, determining threat entry points, and collecting available data of potential threats. The threat model helps the testing team to identify potential vulnerabilities in the blockchain network.
The testing team also performs a risk assessment to identify potential risks associated with the blockchain network. The risk assessment helps the testing team to prioritize their blockchain security testing efforts based on the level of risk associated with each vulnerability.
In this phase, the testing team conducts vulnerability scanning and penetration testing on the blockchain network in order to uncover vulnerabilities and security gaps. When doing vulnerability scans, the testing team makes use of a number of different tools, including Nmap, Nessus, OpenVAS, and others.
In addition to vulnerability scanning, the testing team also conducts penetration testing in order to locate flaws that cannot be found using automated vulnerability scanning techniques. When performing penetration testing, the testing team makes use of a wide variety of tools, such as Metasploit Framework, Burp Suite, and others.
The testing team also performs web application security testing to identify vulnerabilities in web applications that are used by the blockchain network. The testing team uses various tools to perform web application security testing such as OWASP ZAP, Acunetix, etc.
In this step, the testing team attempts to acquire unauthorized access to the blockchain network by exploiting vulnerabilities that were discovered in the previous phase. When doing exploitation, the testing team makes use of a variety of tools such as Metasploit Framework, Burp Suite, and other similar programs.
For the purpose of gaining unauthorized access to the blockchain network, the testing team also engages in social engineering assaults like phishing attacks. In the event that technological vulnerabilities cannot be exploited, social engineering techniques are utilized.
Additionally, the testing team conducts physical security testing in order to locate flaws in the physical security controls that are utilized by the blockchain network. Access control systems, closed-circuit television cameras, and other similar devices are examples of physical security controls.
There are a few key challenges when it comes to blockchain cybersecurity.
The importance of blockchain cybersecurity cannot be understated. Blockchain and security is a critical concept because it is a distributed ledger technology that can be used to store and transfer data securely. Blockchain is often used to store data in a secure and tamper-proof manner, which makes it ideal for storing sensitive data.
Blockchain security is important because it helps protect the data and transactions stored on the blockchain. It also helps to ensure that the blockchain is not susceptible to attacks from hackers. It is, therefore, essential that blockchain security is taken seriously by companies that use this technology. Several measures can be taken to improve security, such as using multiple layers of security, encrypting data, and using digital signatures.
The question “What is blockchain security” is still not understood by many and is a major concern for businesses and individuals who use or rely on blockchain technology. While the decentralized nature of blockchain makes it inherently more secure than centralized systems, there are still potential security risks that need to be considered. These include attacks on the network itself, as well as malicious actors who may try to exploit vulnerabilities in the system. Businesses and individuals who use blockchain technology should ensure that their systems are secure by understanding blockchain and security thoroughly, implementing strong security measures, and keeping up to date on the latest security threats.
A blockchain is like a special file that is shared with lots of different computers. It stores information in a way that’s secure and trusted.
Instead of organizing information like a regular computer file, a blockchain splits the information up into groups called “blocks.” Once a block is full, it gets locked and connected to the previous block, forming a chain of information.
This makes sure that all the information in the chain is very accurate and nobody can change it. It’s also proof of a timeline that can’t be changed once a block has been added. Every time a block is added, it’s given a specific time stamp to show when it was added.
Transactions can be recorded safely and openly in a blockchain, which is a digital ledger. Information is stored in blocks that are cryptographically linked to one another. Each block stores a hashed and encrypted record of transactions or other data. Because each block includes both its own and the hash of the preceding block, the entire chain of blocks can be followed and verified. Signing a transaction using a private key creates a one-of-a-kind digital signature that can only be used once. Within a network, nodes are able to exchange and disseminate data regarding freshly mined blocks.
Blockchain is a technology that can make transactions more transparent, secure, efficient, and traceable. With blockchain, all parties involved in a transaction have access to the same information, which makes establishing trust easier. Transactions are secured through a decentralized network that requires consensus from all nodes before any changes can be made. Blockchain can help prevent fraud and verify the authenticity of assets. It can also reduce costs by eliminating the need for intermediaries and paperwork.
Overall, blockchain is clearly a valuable tool for businesses and industries that require strict security and transparency measures.
Cross Chain Ecosystem Interoperability | NFT Risks and Challenges | Cryptocurrency Mainnet | Types of Sharding Blockchain | List of Wrapped Tokens | Cryptocurrency Faucet | What is Decentralized Application | Ethereum Bitcoin Difference | Ethereum Vs Hyperledger Fabric | CBDC vs Stablecoin | How Does Proof of Authority Work | Blockchain Waves Platform | Hyperledger Fabric Blockchain | What is a Blockchain Transaction | Blockchain Hard Fork vs Soft Fork | Risks of Crypto Lending | Decentralized vs Centralized Crypto | What is Proof of Stake in Sharding Blockchain | EVM Virtual Machines and EVM Chains | Solidity Data Types | Difference Between Cryptocurrency and Blockchain | Best Blockchain Explorers | What Is Tokenomics | Layer 1 Blockchain | Best Crypto Faucets